Site owners are often shocked to discover that there’s a constant stream of attempted logins from bots and hackers trying to gain access for malicious purposes. WordPress is somewhat lacking in login security, so being blissfully unaware of this is a good reason why sites often don’t have good security measures in place.
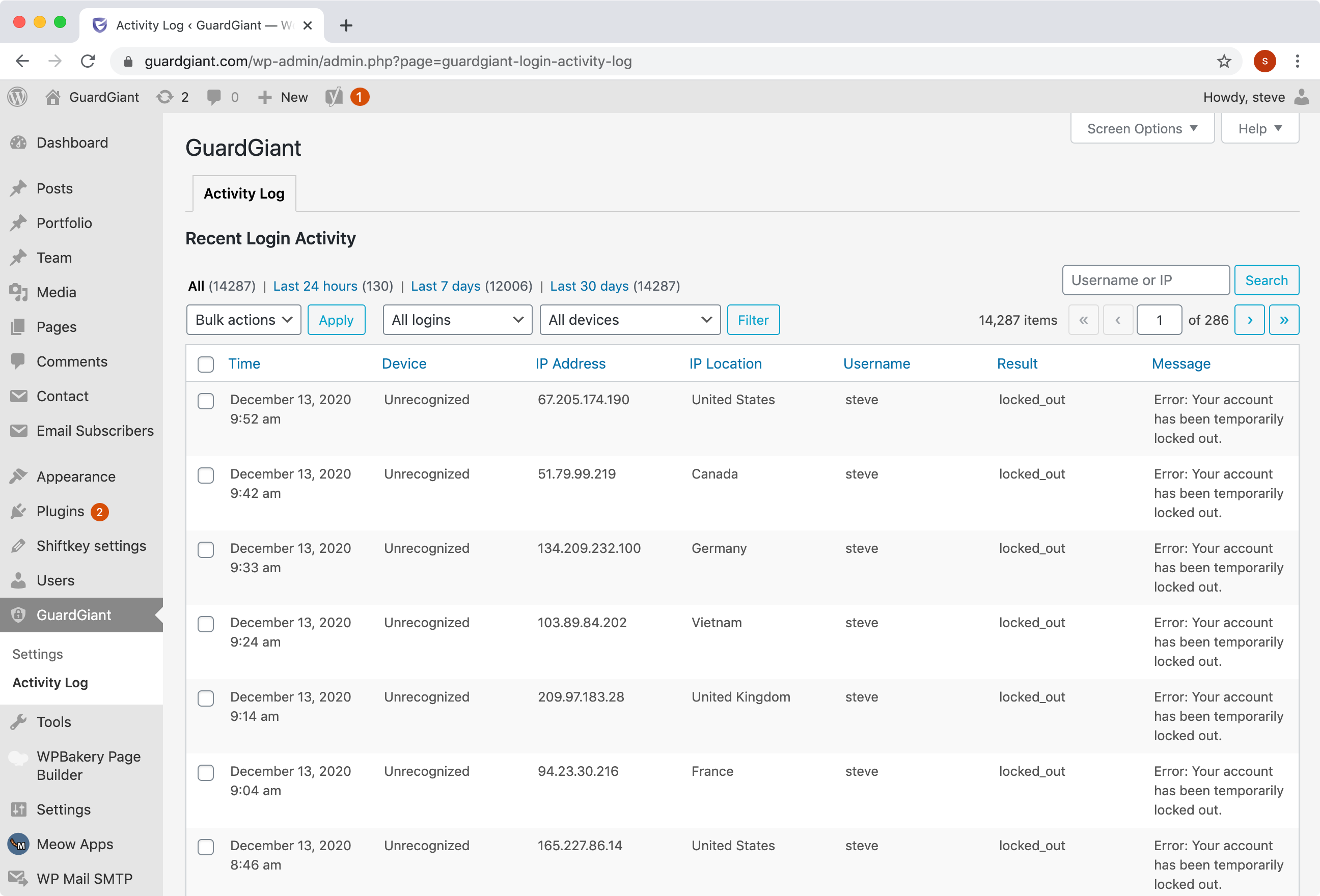
Reviewing user login activity will help to establish visibility into potential security issues. In the event of a hack, the login activity log is essential for troubleshooting and trying to identify what happened.
Our own site has had over 12,000 log in attempts in the last 7 days. Only a handful of those were made by genuine users; the rest were attacks on the site.
Larger sites will be specifically targeted by attackers and will have many, many more login attempts.
In this article, you’ll learn about the 3 things you should monitor in your Login activity log.
Get Started
We are going to install the GuardGiant plugin to give us the activity log. Head to https://wordpress.org/plugins/guardgiant/ to install the plugin.
A GuardGiant menu will appear in your menu bar, with a settings page and the activity log.
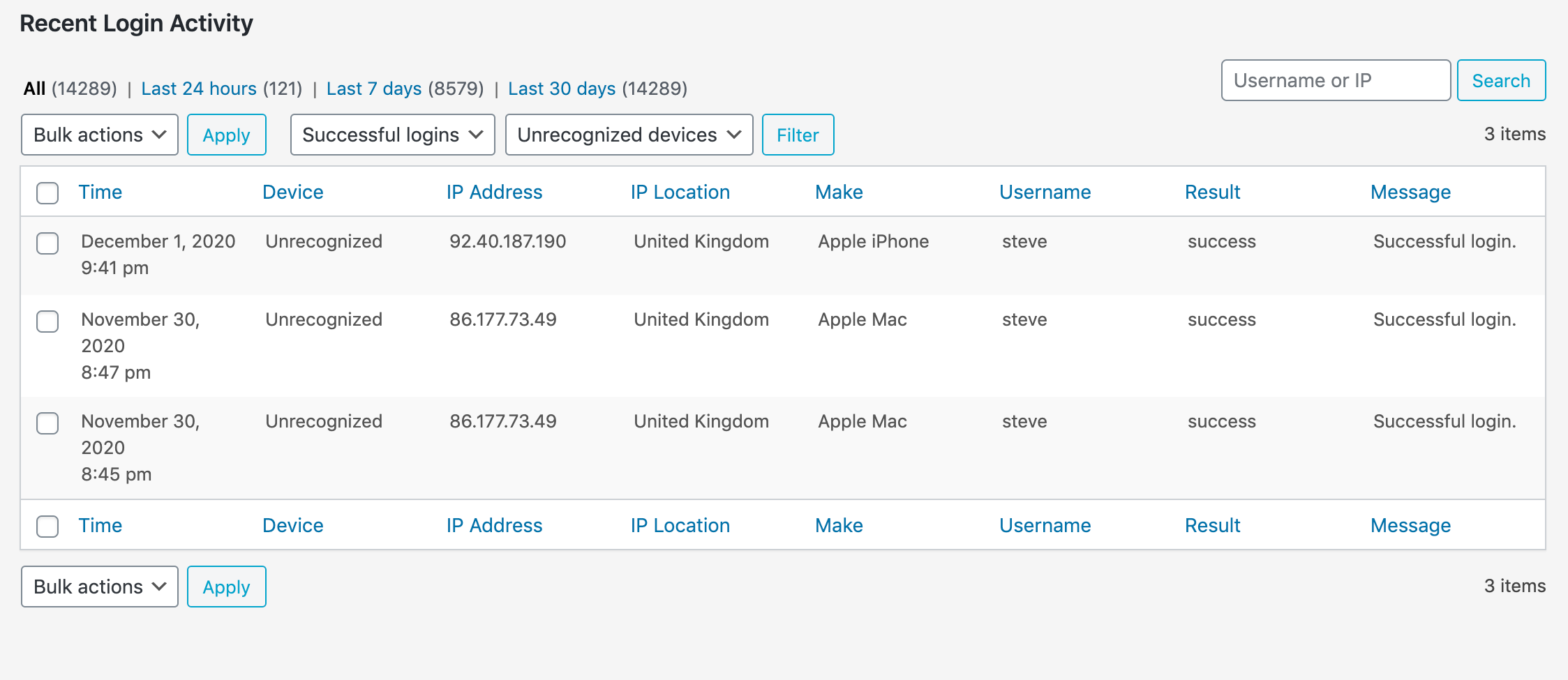
1 – Watch out for successful logins from unknown devices
One of the great things about GuardGiant is that it remembers the devices that your users use to login. If a user has previously logged in using a particular device, you don’t need to worry too much from a security standpoint if they forget their password and make a failed login attempt using the same device.
What is more interesting is if a user logs in with a new device that has not been seen before. If this was preceded by multiple failed attempts over a sustained period of time this could very well indicate a breach of the account.
You can easily filter the activity log to show these logins by selecting both ‘Successful logins’ and ‘Unrecognized devices’ from the filter dropdown menus.
2 – Know who is logging in
Knowing who is logging in and when is important because it help to detect unusual behaviour that could indicate a compromised account.
Select ‘Successful logins’ from the filter dropdown menu to list all successful logins by any user. The table is sorted by time and date by default.
An interesting view is to sort the table by IP location – a login from an unexpected country is a good indicator of trouble.
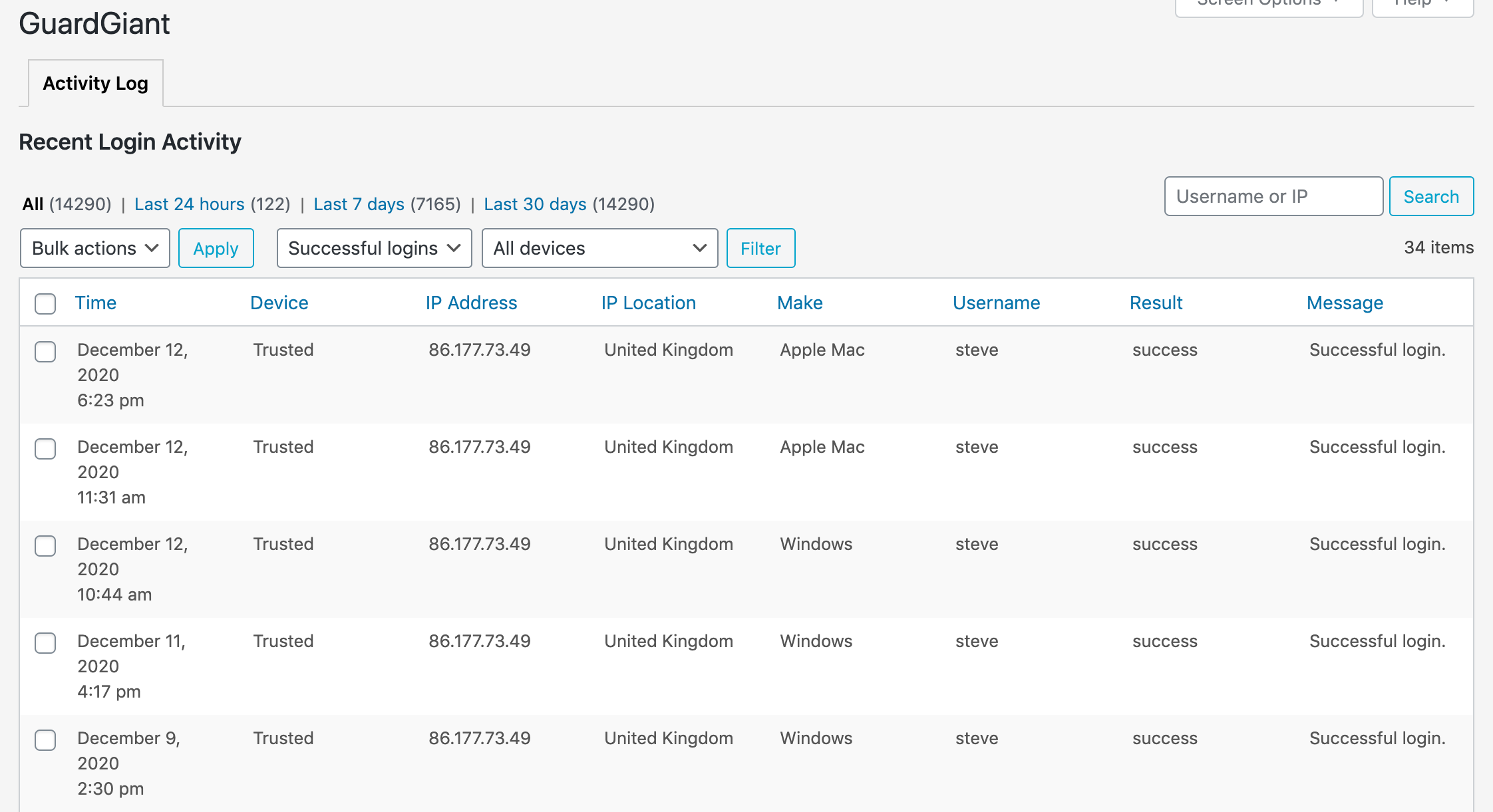
You can sort the table by username to review the users that have logged in. Should every user on there be logging in? Sometimes temporary or development accounts are created and then forgotten about, leaving a door open for attackers.
3 – Investigate suspicious activity
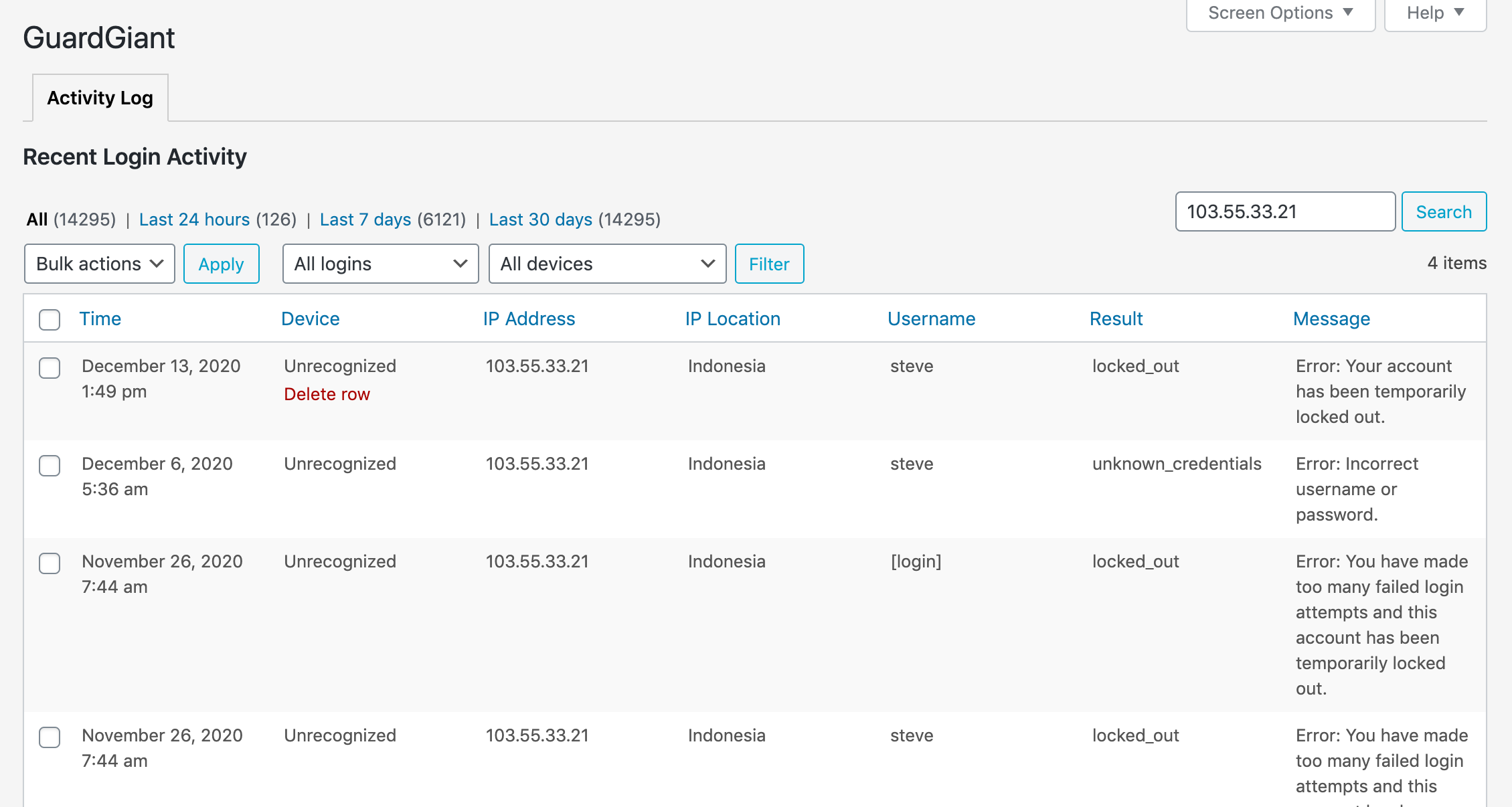
Having visibility to login activity should be an important element of your security plan. A quick glance at the log from time to time will often show up activity that looks suspicious. If a particular IP address is giving cause for concern you can easily search for all related logins in the search box.
Conclusion
In this post, we explained the importance of having visibility to login activity and the key metrics to track.